When you provision an Entra ID application which you are developing or using for unattended operations, you must have two things: a client id and a credential to prove you are the application.
For the application, you will need to decide on one of two options:
- A client secret (passwordCredentials)
- A certificate (keyCredentials)
Both options have an expiration, so you can’t just set this up and ignore it–you must maintain it. You don’t want to set it up and learn a lesson a year later when that credential expires.
The simple option is client secret. This is the best option for an application for unattended operations. With this option, you can choose how long the secret will last until it expires.
Note: Never was an option for a brief period, but is not generally appropriate and was discontinued. If you chose "never" there may come a time when Microsoft decides your credential is no longer valid--we recommend you replace it with a fixed time-period credential to avoid this possibility..
The harder option is the certificate. This may be a good option if you are developing code. This option requires that your app possess the private key for a cert and that you provision the public cert in Entra ID on the app. We don’t cover how to do that here. The expiration depends on the certificate’s expiration.
What follows is a step-by-step description of how to setup and maintain a client secret for an Entra ID service principal:
- You need to start at the Azure Portal (there are other administrative interfaces you might use, but this description uses the Azure Portal): https://portal.azure.com
- Sign in using the account which has permissions for the administrative task you want, usually a sadm admin UW NetID. For this task, this will be whatever account created the service principal.
- Open ‘Entra ID’ by searching for it, unless it is already in your top nav bar.
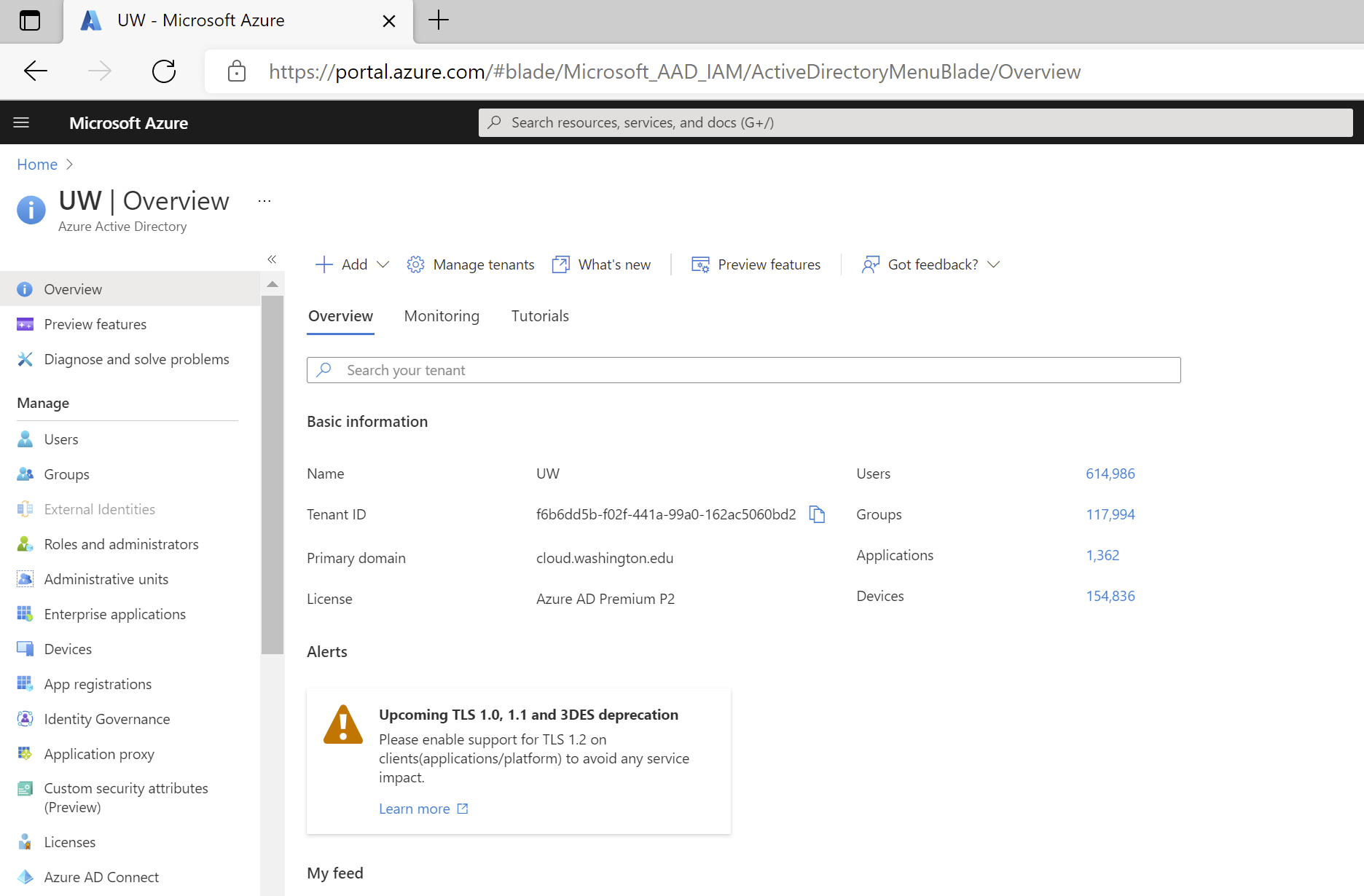
- Choose ‘App Registrations’ from the left nav bar. A short cut to the resulting page is https://portal.azure.com/#blade/Microsoft_AAD_IAM/ActiveDirectoryMenuBlade/RegisteredApps. In other words, you can jump directly to this step (you still have to do #2) by using that URL.

- Enter the appId or displayName of your service principal in the search field. If you don’t know your appId or displayName, you may need to create a new service principal.
- Select the right service principal from the results.
- Choose ‘Owners’ from the left nav bar. Verify that the account you used in #2 is the owner. Ideally you will add a 2nd account as an owner so that if you are unavailable or have left, someone else can maintain this application.
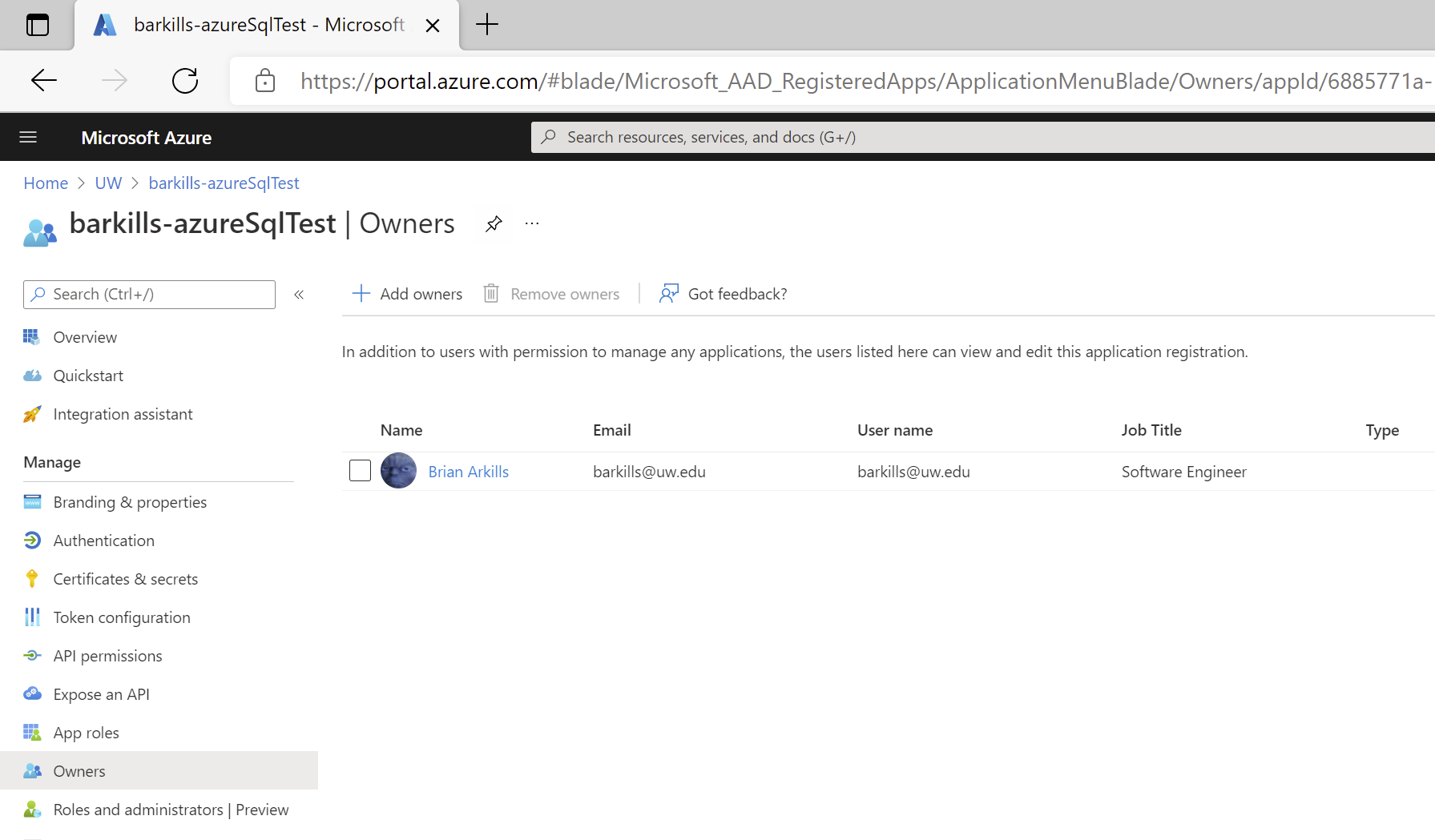
- If you are the only account, fix that now.
- If you didn’t use the right account for #2, logout and start over with the right account.
- Choose ‘Certificates & secrets’ from the left nav bar.
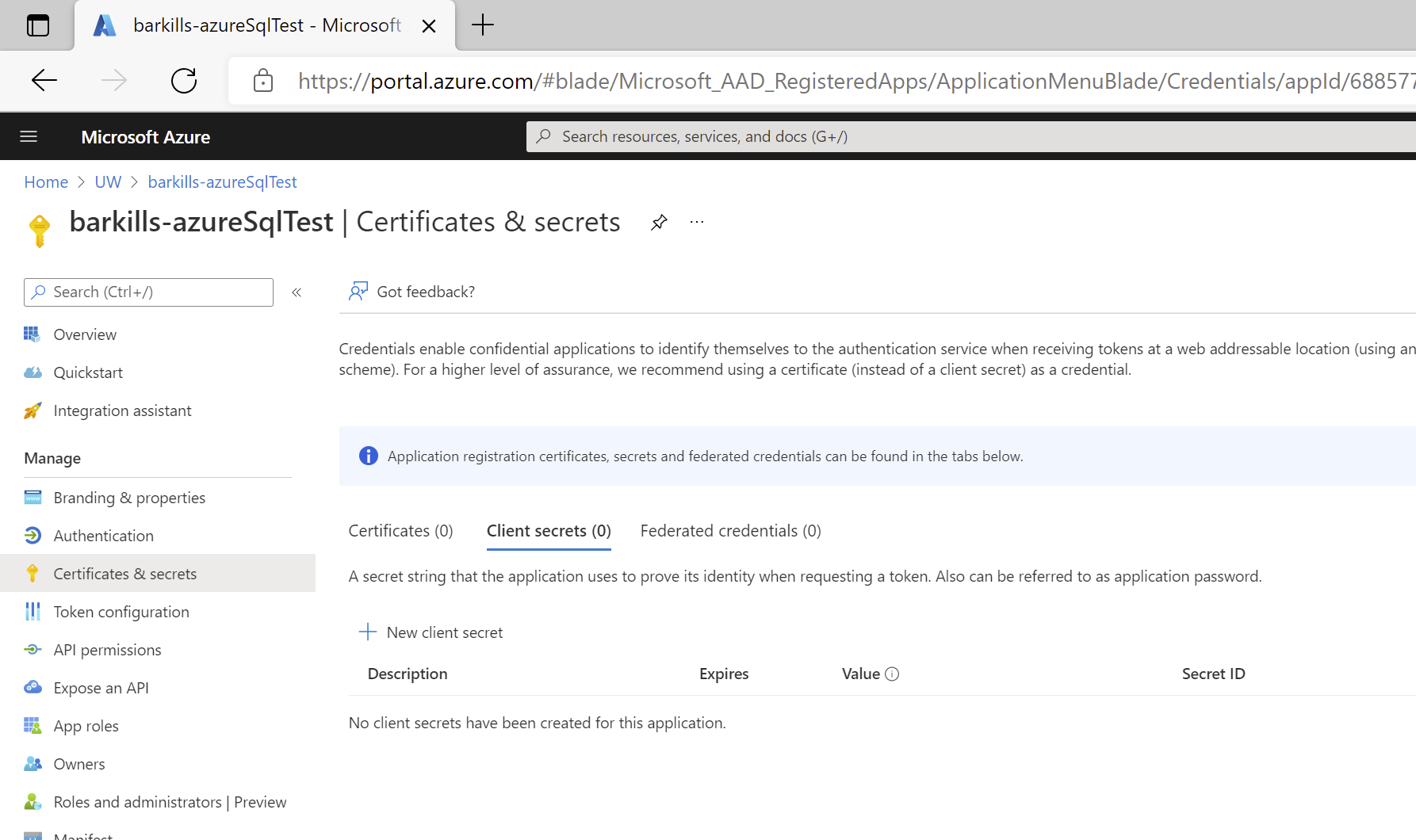
- Note whether there is a secret or not. Some service principals have none, which makes them worthless—you can’t do anything with the service principal without signing in with it.
- If there is no secret, click ‘New client secret’.
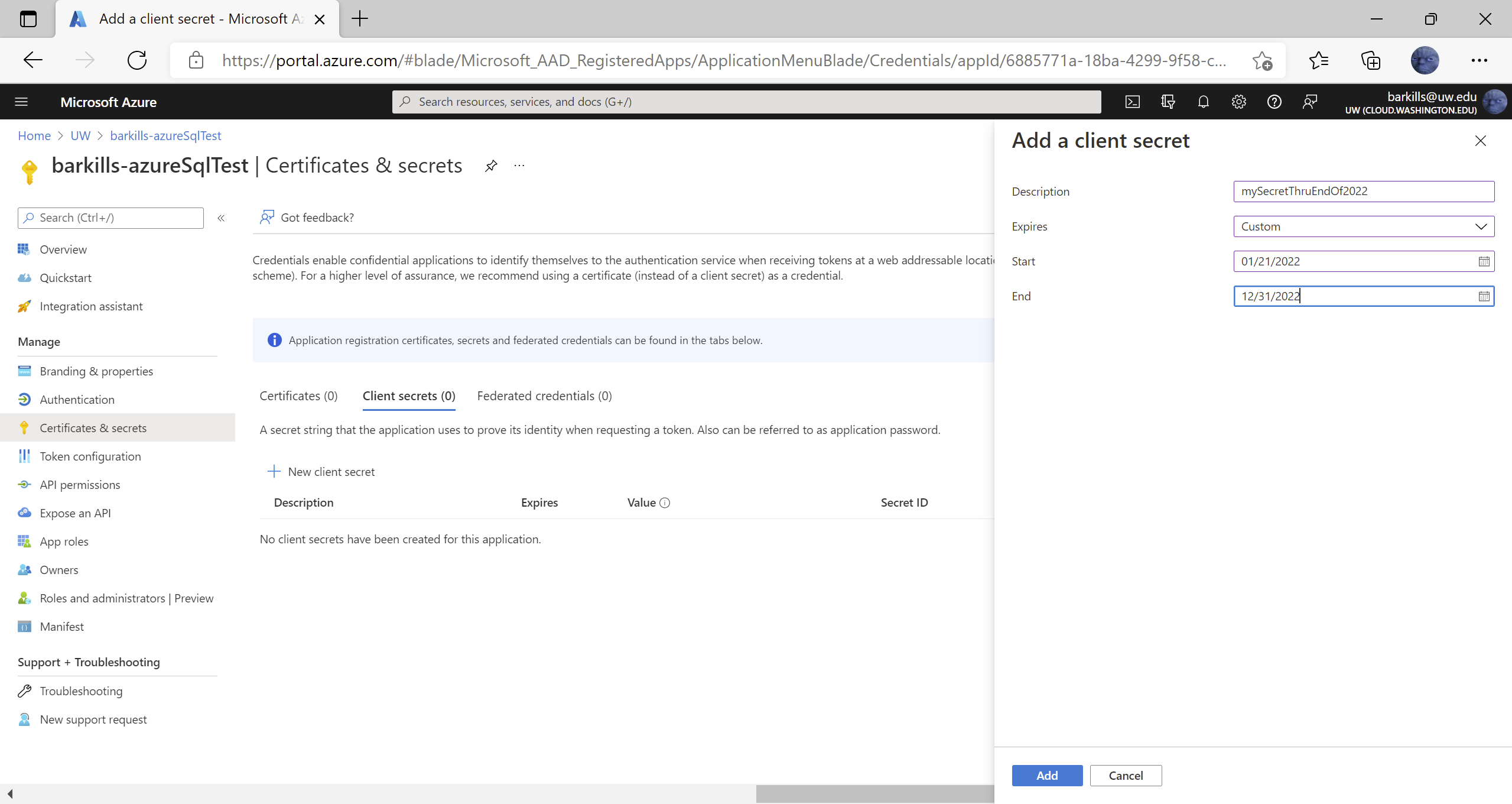
- Enter a description that’ll be useful to you and choose an expiration period.
- If you need to share this secret with someone who is not an application owner, copy the secret’s value to a safe place, like a password manager. UW has LastPass Enterprise which would be a good place to store & protect this secret and share with others who need it.
- If there is no secret, click ‘New client secret’.
- Note the date in the Expires column.
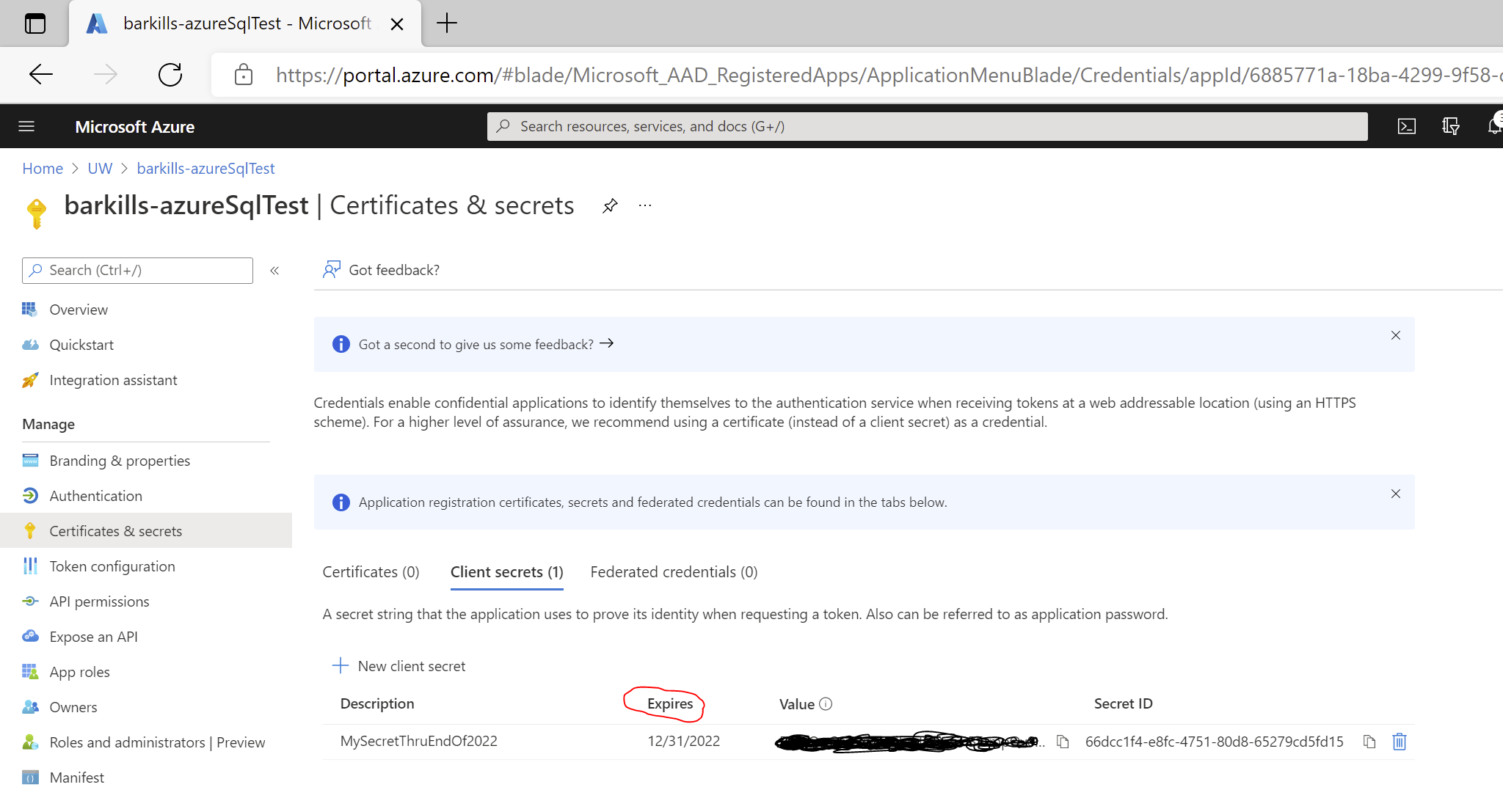
- Keep track of this expiration date and plan to come back to get a new secret before that date.
