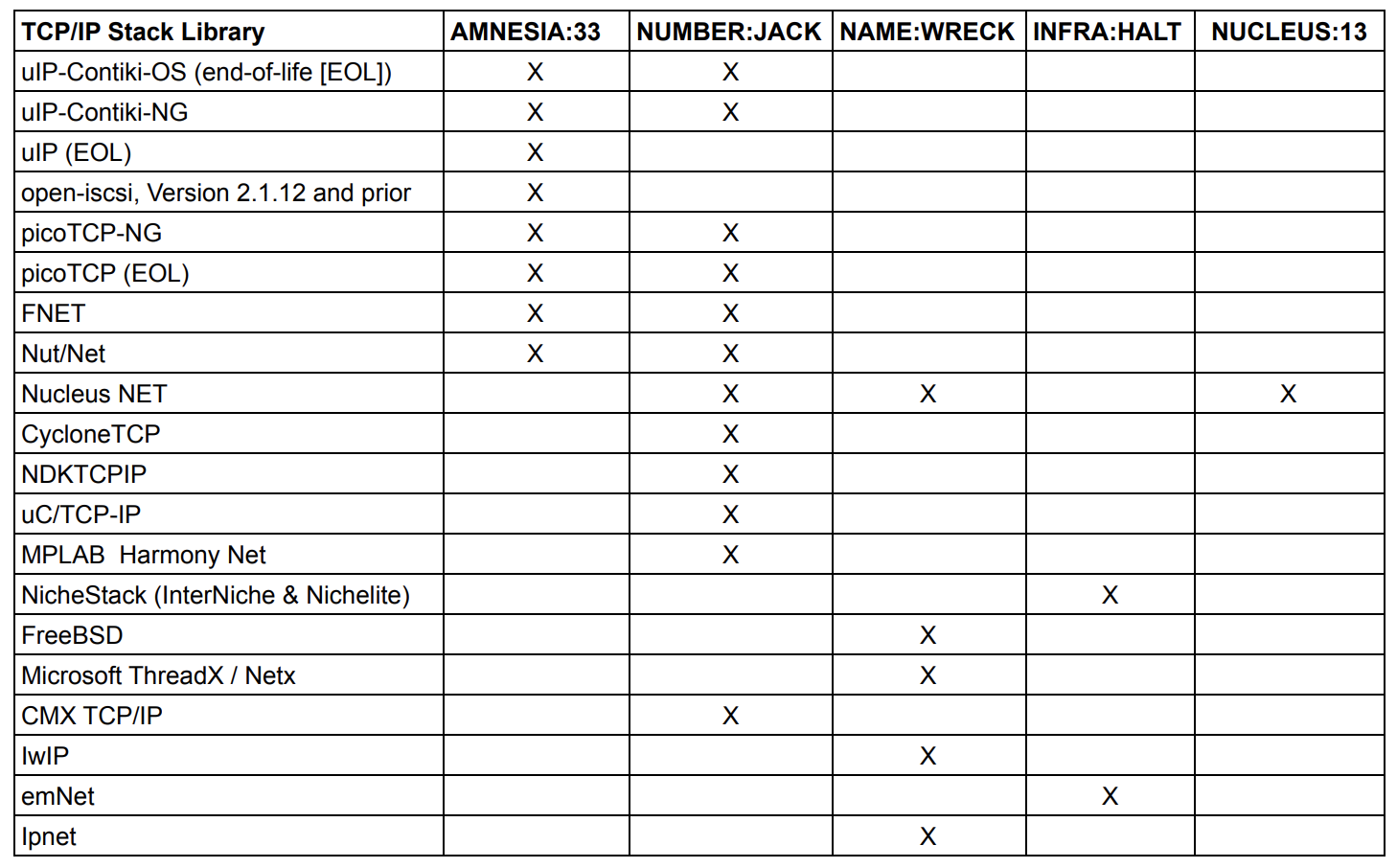
Below is a list of known compromised TCP/IP stack libraries and Real-Time Operating System (RTOS) products with known vulnerabilities. These particular libraries are found in millions of IoT devices and over 170 vendors.
It is strongly recommended to have your vendors confirm that the following vulnerable TCP/IP stack libraries and/or RTOS are not embedded in the IoT / IIoT / OT / ICS product you are purchasing (e.g. HVAC, lighting controls, classroom technology, research systems, access controls, video surveillance systems, and other). If one or more of these software library versions are in a system that you own, it is strongly recommended that you work with your vendor to identify software upgrades, replacements, or other remedies.
Disclaimer: This list is derived from Forescout Research Lab’s Project Memoria and is not an exhaustive list of IoT vulnerabilities. Further, this list focuses on TCP/IP stack vulnerabilities versus others.