Entra ID applications are an identity which allows software to take advantage of Entra ID capabilities.
| Topics on this Page: | Related pages you might be interested in: |
What you Might Need to Know as a User of an Entra ID Application
As a user of Entra ID, you might need an Entra ID application. These will typically be one of three types of scenarios:
- You would like to use 3rd party software via Entra ID
- You are a developer writing software and want to integrate via Entra ID
- You would like to leverage an Entra ID capability for your existing software
Using 3rd party software via Entra ID
You’ve found a 3rd party software that needs to be integrated with the UW’s identity system and possibly also integrated with other Entra ID applications. This may be a web application, a phone “native” app, or even an Office add-in which also has an installable download.
There are usually two steps:
Adding software as an Entra ID application
The details about how a user might self-provision an Entra ID application identity happen to differ greatly depending on the application (just as it does for integration with any other identity solution), and it isn’t always obvious to users when Entra ID is involved.
Some examples:
- Microsoft has a gallery/catalog of more than 3000 “pre-integrated” SaaS applications, where they’ve already done the hard work to connect whatever authentication that software uses to Entra ID authentication. This means the UW identity integration cost is minimal. In some cases, the Entra ID integration even handles user provisioning in the 3rd party web application’s custom user system, meaning you don’t have to do that work separately. Many of the 3rd party applications in that gallery require you to separately establish a customer relationship with the vendor and in such cases you many need to restrict user assignment of the applications to those you are willing to pay for. There are some additional costs associated with restricting assignment, so you are encouraged to first talk with UW-IT about that kind of scenario.
- Other vendors may not be in Microsoft’s gallery/catalog, but do enable you to create the necessary Entra ID application identity to enable UW use by clicking to enable/install them. The software which uses that identity may be on your local computer or on a web site. One innocuous example of this is an Office Add-on called FindTime. Not all of these kinds of ‘click to enable’ Entra ID application identities are located in the Office Store.
Some Entra ID applications require an admin to grant permissions before they can be created.
If you choose to add or consent to an Entra ID application provided by a third party, there is a risk that UW confidential data may intentionally or unintentionally be accessed, collected, or used by the third party. UW organizations are responsible for evaluating the risk and implementing controls for their unique technical deployments.
If you’ve evaluated the risk and decided to use a third party application, then it should meet the UW data security and privacy goals for contracting with vendors. This may include the need for a Data Security and Privacy Agreement or a Business Associate Agreement. Additional responsibilities may be required by UW Medicine for use of Entra ID applications with protected health information. If you’d like help analyzing third party applications or adding an Entra ID application, please contact UW-IT at help@uw.edu.
Consenting to the permissions an Entra ID application requires
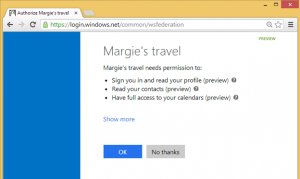
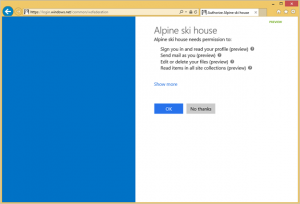
When a user tries to access an Entra ID application identity that requires permissions to other Entra ID applications, a user consent prompt is presented. This prompt is provided by Microsoft, not the 3rd party.
The prompt contains a list of the permissions requested by the application, and the user can accept or decline. Acceptance results in permissions granted and recorded for that user. Declining blocks access to the Entra ID application.
Users working with confidential data are strongly encouraged to take care about consenting to permissions when the application you are granting access to lacks proper controls.
If you aren’t sure, you should ask for help by contacting UW-IT at help@uw.edu.
Some example screen shots of this experience:
Developer integration via Entra ID
You are a developer writing software. You either need to leverage the API of an Entra ID application or you need to authenticate users and would like to use the modern protocols that Entra ID supports.
Microsoft’s Integrating applications with Entra ID is a good introductory resource for developers seeking to integrate using an Entra ID identity. Developers seeking to leverage Microsoft Graph or Office 365 APIs may find this TechNet article useful. There is now also a preview Entra ID PowerShell module which allows creation and manipulation of Entra ID applications.
Augment your existing software with Entra ID capabilities
You have some existing software which you’d like to benefit from one of the capabilities that Entra ID provides. The most likely capabilities you might want to leverage are: Entra ID Conditional Access, Azure MFA, Entra ID logging and security reporting, single sign-on for a scenario that allows an existing Integrated Windows Authentication web app (this capability is called Entra ID Application Proxy), or simply having your application listed in a user-focused application portal which has single sign-on like benefits.
For any of these scenarios, you should talk to UW-IT.
Entra ID application which require admin approval
Some Entra ID applications require permissions which other applications have defined to require an Entra ID tenant admin to explicitly approve. These applications can not be added by a user themselves.
Additionally, there may be additional permissions which the UW decides are risky, even if vendors don’t identify them. When we detect an Entra ID application which has those risky permissions, we will disable that Entra ID application and it will go through a risk evaluation & acceptance process like the one required for Entra ID applications that require an Entra ID tenant admin to explicitly approve them.
If you think you have such an Entra ID application, you can use the request form for that.
If you’d like to read more about what UW considers risky Entra ID permissions and how you might request a change to what we consider risky, please see our Risky Entra ID application permissions page.
Microsoft endorsed Entra ID applications
In addition to these scenarios, there is another type of Entra ID application, which is mostly commonly called a “first person” application. These are Entra ID applications that Microsoft provides, like Exchange Online. These Entra ID applications sometimes don’t follow the guidelines noted above, and there may be extra limitations or per user licensing required.
Reference material:
https://docs.microsoft.com/en-us/azure/active-directory/develop/authentication-scenarios
https://docs.microsoft.com/en-us/azure/
‘Modern Authentication with Azure Active Directory for Web Applications‘ by Vittorio Bertocci