Managing Windows Firewall settings at scale saves time while broadly providing protection from internet based attackers. This document describes how delegated OU customers can create and update a group policy object which uses current definitions of the UW network. This can be useful in only allowing specific network access from computers on the UW network.
Three different ways to approach this task are described:
Creating a GPO to enable Windows Firewall settings using GPMC.MSC
Creating a GPO to enable Windows Firewall settings with Powershell
Updating an existing GPO for Windows Firewall with Powershell
Creating a GPO to enable Windows Firewall settings using GPMC.MSC
This particular example enables traffic to TCP port 8888 from all of UW Campus, but you can choose whatever ports are needed for your scenario.
Using gpmc.msc, navigate to the OU where you want the GPO applied. Right-click and select “Create a GPO in this domain, and Link it here”.
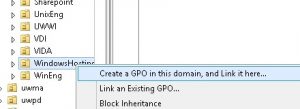
Note: Ensure you are following the GPO naming conventions as detailed here: /tools-services-support/it-systems-infrastructure/msinf/design/policy/ou-practices/#groupPolicy
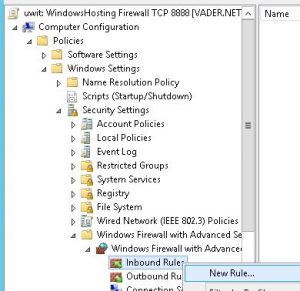
In the right pane, “Edit” your new GPO. Navigate to the Windows Firewall section under Computer Configuration->Policies->Windows Settings->Security Settings->Windows Firewall with Advanced Security. Right-click Inbound Rules and select “New Rule”
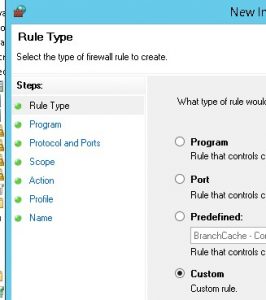
Select “Custom” for Rule Type.
For Protocol and Ports, select TCP and enter 8888 for specific local ports. You can enter multiple ports or port ranges in these boxes.
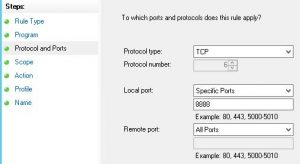
For Scope, enter the subnets as defined by UW Network Operations in the remote IP addresses section. The full list can be found at https://wiki.cac.washington.edu/x/AH0rAw.
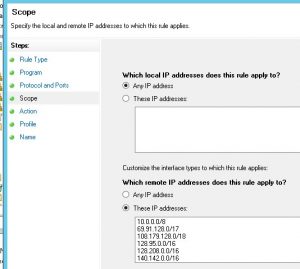
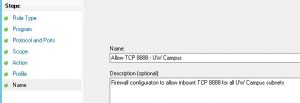
Click through the wizard adjusting as necessary and provide a Name. In this example, the name “Allow TCP 8888 – UW Campus”
Creating a GPO to enable Windows Firewall settings with Powershell
The following PowerShell code sample can be used to create a group policy object with the Windows Firewall settings.
The code references CampusIpRanges.txt which contains a list of current IP address ranges as managed by UW-IT’s Network Operations team. The Microsoft Infrastructure service updates the CampusIpRanges.txt file quarterly. Changes will also be made when there is customer notification of changes to the following authoritative source: https://wiki.cac.washington.edu/display/UWNOC/IP+Address+Space+Usage
# Sample Powershell code to parse an existing text file with UW Campus IP ranges and create a GPO enabling Windows Firewall
# Current list of UW Campus IP ranges can be found at \\netid.washington.edu\netlogon\CampusIpRanges.txt
#
import-module grouppolicy
$IpAddressListFile = '\\netid.washington.edu\netlogon\CampusIpRanges.txt'
$UwCampusIps = New-Object Collections.Generic.List[String]
$lines = Get-Content $IpAddressListFile
foreach ($line in $lines) {
if ($line -match "^s*#") {
continue
}
elseif ($line -match "^s*$") {
continue
}
elseif ($line -match "^([0-9./:a-f]{7,25})s*(#.*)?$") {
Write-Output $matches[1] $UwCampusIps.Add($line)
}
else {
Write-Output ("IGNORED: " + $line)
}
}
#
# to create a GPO called "pottery: Firewall TCP 8888" which allows inbound TCP 8888 from UW Campus IPs and link it to the OU of Delegated/pottery
#
$FwRule = "Allow TCP 8888 - UW Campus"
$GpoName = "pottery: Firewall TCP 8888"
$TargetOU = "OU=pottery,OU=Delegated,DC=netid,DC=washington,DC=edu"
$PolicyStoreName = "netid.washington.edu\" + $GpoName
New-Gpo -Name $GpoName | New-Gplink -target $TargetOU
$GpoSessionName = Open-NetGPO –PolicyStore $PolicyStoreName
New-NetFirewallRule -DisplayName $FwRule -RemoteAddress $UwCampusIps -Direction Inbound -GPOSession $GpoSessionName -PolicyStore $GpoName -Protocol TCP -LocalPort 8888
Save-NetGPO -GPOSession $GpoSessionName
Updating an existing GPO for Windows Firewall with Powershell
CampusIpRanges.txt contains a list of current UW IP address ranges. The Microsoft Infrastructure service updates the CampusIpRanges.txt file quarterly. Changes will also be made when there is customer notification of changes to the following authoritative source maintained by UW-IT’s Network Operations team: https://wiki.cac.washington.edu/display/UWNOC/IP+Address+Space+Usage
The following sample code can also be found in \\netid.washington.edu\netlogon\CampusIpRanges.txt as a reference.
You can use this Powershell code to either perform a one-time update of an existing GPO or customize it to run as a script to dynamically update your rules as changes occur in the UW Campus IP address space.
# Sample powershell code to process file and build a list ($UwCampusIps) to be used as input for the Set-NetFirewallRule command for the parameter -RemoteAddress
import-module grouppolicy
$IpAddressListFile = '\\netid.washington.edu\netlogon\CampusIpRanges.txt'
$UwCampusIps = New-Object Collections.Generic.List[String]
$lines = Get-Content $IpAddressListFile
foreach ($line in $lines) {
if ($line -match "^s*#") {
continue
}
elseif ($line -match "^s*$") {
continue
}
elseif ($line -match "^([0-9./:a-f]{7,25})s*(#.*)?$") {
Write-Output $matches[1]
$UwCampusIps.Add($line)
}
else {
Write-Output ("IGNORED: " + $line)
}
}
#
# to select an existing GPO called "pottery: Workstations: Test Firewall" and modify an existing Advanced Firewall Rule named "Allow all 8080"
#
$FwRule = "Allow all 8080"
$GpoName = "pottery: Workstations: Test Firewall"
$GpoSessionName = Open-NetGPO –PolicyStore $GpoName
Set-NetFirewallRule –DisplayName $FwRule -RemoteAddress $UwCampusIps –GPOSession $GpoSessionName
Save-NetGPO -GPOSession $GpoSessionName