- Introduction
- Chapter 1: Requirements
- Chapter 2: Setting Up Your Domain
- Chapter 3: Setting up the domain controllers
- Chapter 4: Removing a domain controller
- Chapter 5: Where to go from here
Introduction
Purpose of this document
This document is intended for support personnel or system administrators at the University of Washington. It covers setting up a Windows 2000 domain controller that will be linked into the UW’s existing DNS structure. This document does not cover the details of setting up and using Windows 2000; it assumes that you are already familiar with the basics of using Windows 2000.
NOTE: While Windows 2000 is no longer current, the basics remain the same and this document remains relevant.
A note about the term “domain”
Throughout this document the word domain will sometimes refer to a DNS domain and sometimes refer to a Microsoft Windows domain. While in the past these two concepts were separate and non-interchangeable, that is not as true today. With Windows 2000, Microsoft has adopted the DNS naming conventions and structures to its domains. For example, the domain name “cs.washington.edu” is both the DNS and Windows 2000 domain name for Computer Science. For most purposes, these terms are now interchangeable.
We recommend that you read Windows Domain DNS reliance before setting up a Windows domain.
Chapter 1: Requirements
The following chapters of this document assume that you have already performed certain requirements. Those requirements and how to get more help in fulfilling them are outlined below.
Authority to run the domain controllers for your intended DNS domain
In Windows, the windows domain naming structure parallels the DNS naming structure. Thus, the authority and responsibility for the DNS and windows domains are one and the same. If you are unaware of the contact for your department’s DNS domain, wish to change the contact person for your department, or wish to register a new department, send email to help@uw.edu.
Windows Servers installed as a stand alone servers
You should have at least two servers ready to act as domain controllers. These machines should not be used as workstations or provide other network services since their stability and availability are paramount. The reason for having more than one domain controller is that if all of your domain controllers become simultaneously unavailable, users cannot log in to your domain. Additionally, if all of your domain controllers become simultaneously unrecoverable, your domain will have to be recreated from scratch.
The domain controllers do not have to have a great deal of computing horsepower. Two domain controllers should be adequate for typical domains serving around a hundred users provided they are only acting as domain controllers. It is easy to add and/or upgrade domain controllers in the future should you find that you require more capacity.
A static IP address and DNS name assigned to your intended DCs
Since your domain controllers must be found by workstations wishing to log into your domain, they must be registered with static IP addresses and have a DNS name in your intended domain. Most DNS changes, including ones like this are self-service for the registered contacts via https://networks.uw.edu/.
Chapter 2: Setting Up Your Domain
Authorize your domain
In order to maintain the domain controllers for a domain, you must be the domain contact person. Every existing DNS domain already has a contact person listed. If you are unsure of your domain contact person, you can contact Network Operations to find this out. If you are the domain contact, the registered contacts for your DNS zone can register those domain controllers self-service via https://networks.uw.edu/, so that other computers can find them. This process is outlined below.
If you have questions about the DNS domain contact system, you can send email to help@uw.edu.
Register your domain controllers
Initially, you’ll need to add one host record (A) for each intended domain controller in your new Windows domain. Then you’ll also want to specify that those domain controllers respond to host requests for your DNS domain. The registered contacts for your DNS zone can register those domain controllers self-service via https://networks.uw.edu/.
For example, if my intended Windows domain is pottery.washington.edu, with clay & shard as the domain controllers, then I’ll want the following:
Host (A) records:
- clay.pottery.washington.edu <static IP for clay>
- shard.pottery.washington.edu <static IP for shard>
- pottery.washington.edu <static IP for clay>
- pottery.washington.edu <static IP for shard>
These are not all of the DNS records needed, but these are important for a variety of basic purposes and necessary to run the domain controller promotion process. See more later about additional DNS records.
Chapter 3: Setting up the domain controllers
For each of your domain controllers, you should follow the steps in this chapter. Some steps will have alternate actions depending on if you are joining an existing forest.
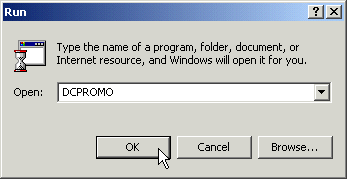
Run DCPROMO
From the Start menu of your domain controller, select run and enter: DCPROMO
This will start the Active Directory Installation Wizard.
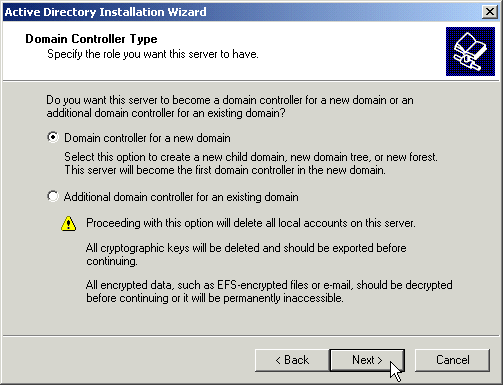
If this is the first domain controller in your domain, choose “Domain controller for a new domain”. If this is not the first one you have set up, choose “Additional domain controller for an existing domain, click next, and authenticate to your existing domain.
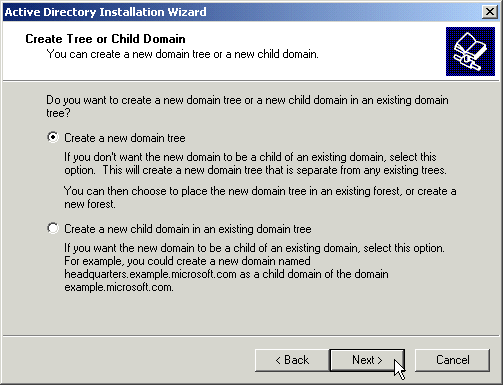
Choose “Create new domain tree”, even if you will be joining an existing forest.
If you are joining an existing forest, choose “Place this new domain tree in an existing forest”. Otherwise, choose “Create a new forest of domain trees”.
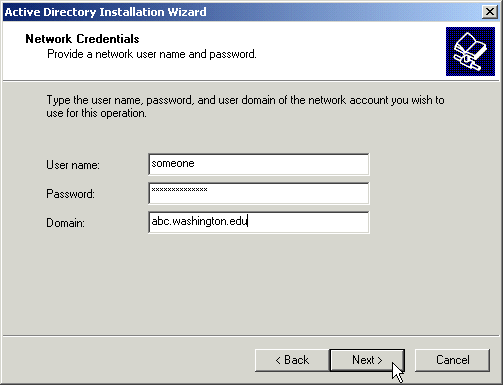
If you are joining an existing forest, you will be asked for credentials to use to join. You will need to get this information from the administrator of the forest you are joining. This account must have authority to add domains to the forest.
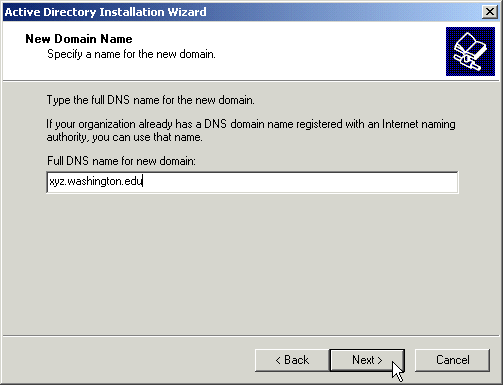
Enter the name of your domain.
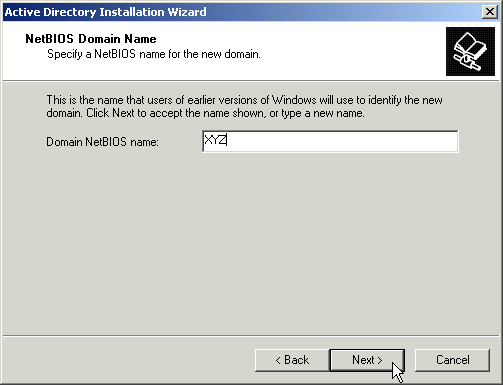
Specify a NetBIOS name for your new domain. This name will be used by older operating systems (Windows 98, NT 4.0, etc.) should you choose to support those operating systems.
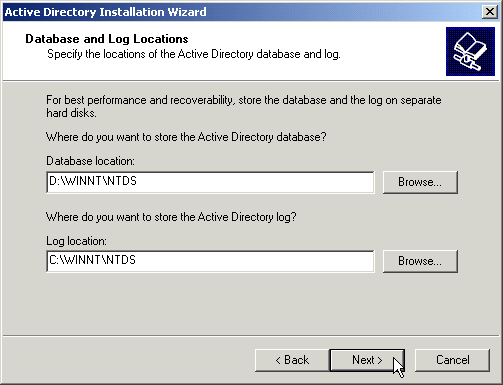
If you have separate physical hard disks, it’s a good idea to keep the database and log on separate disks. Otherwise, one could slow the other down.
Enter a directory for the public files area of your Active Directory tree.
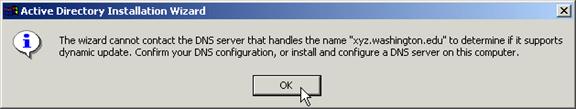
At this point, you may see the following message. You can safely ignore this, as you will be sending DNS registration information in a later step.
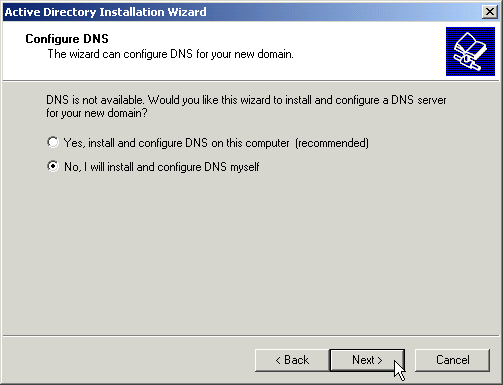
Choose No, you will be configuring this later.
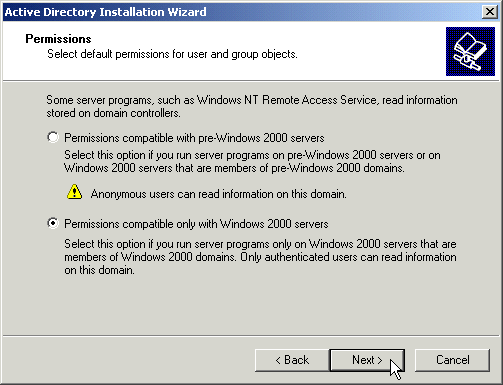
Unless you have a mixed environment with Windows NT 4.0 servers that use Active Directory information, you should choose to set the more strict Windows 2000 only permissions.
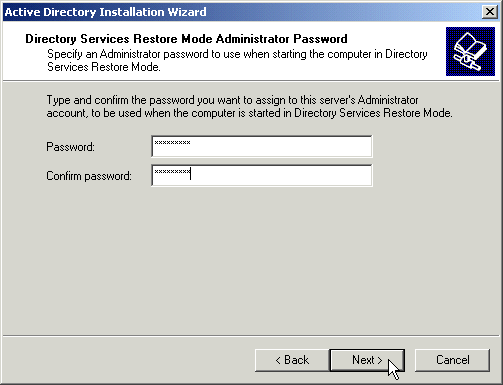
Enter a password to be used if you must restore the Active Directory. This will also be your initial administrator password.
Review your setup and click next to start the configuration process. You will see a screen similar to the following for a few minutes.
When the configuration process completes, you will be directed to restart your computer. After your domain controller restarts, log in to your new domain as administrator.
Update DNS information
Find the file NETLOGON.DNS from your domain controller’s <WINDIR>\SYSTEM32\CONFIG directory. <WINDIR> will usually be C:\WINDOWS.
Each line in this file has a DNS record that you must ensure is properly registered. Failure to get these records registered in DNS will lead to significant functionality problems, including the inability for domain joined computers to find the domain controller, replication problems between domain controllers, failure to be able to trust another domain, an inability to change passwords, and more. DNS misconfiguration is the #1 cause of Active Directory problems.
Note: every line in the file is important. There will be CNAME, SRV, and A records in this file. You may not be familiar with some of these record types. You may think they look funny, but every one of them enables an important capability. Don’t skip any!
The registered contacts for your DNS zone can self-service register each line in this file for each domain controller via https://networks.uw.edu/.
For SRV records, translating each line in the netlogon.dns file to what the networks.uw.edu interface wants can be a challenge. Here’s a step-by-step breakdown of what to do:
Let’s say your first line is:
_ldap._tcp.pottery.washington.edu. 600 IN SRV 0 100 389 DC-01.pottery.washington.edu.
Here’s what you’ll do:
- Click on DNS Resources
- Click on pottery.washington.edu domain
- Click on Add
- Enter the name at the start of the line. So for that first row: _ldap._tcp.pottery.washington.edu. Click Next.
- Click ‘Add record’
- Choose type: SRV
- Change TTL to the first number in the line (600 in our example)
- Set priority to the second number in the line (0 in our example)
- Set weight to the third number in the line (100 in our example)
- Set port to the fourth number in the line (389 in our example)
- Set target server to the hostname at the end of the line (DC-01.pottery.washington.edu in our example)
- Save.
- Go back to step #5 (add record) and repeat for each line.
Several of the lines are not SRV records–a few CNAME records and at least one A record. Those should be more straightforward.
Note: UW-IT will not make these changes for you any longer–please make these changes yourself.
Turn Off Dynamic DNS
By default, a Windows domain controller will try to periodically update its DNS server with new information. Since the DNS servers at the UW do not accept dynamic updates, this will cause unnecessary network traffic and trigger error events in your event logs.
To turn off dynamic DNS updates on a domain controller:
You should disable (uncheck) the “Register this connection’s addresses in DNS” setting. This property can be found in the DNS tab of the Advanced TCP/IP Settings dialog in the properties of your local area network connection.
This should be done on every network interface for the domain controller.
If you would like information on how to turn off DNS updates on your workstations using group policy objects, see Microsoft Knowledge Base article Q294832.
If you are not using the UW’s DNS servers and are running your own DNS servers that support dynamic updates, you can disregard this section.
Configure a time server
Since Windows Active Directory uses Kerberos authentication, having the correct time is critical. If this is the first domain controller you are setting up, you must give it an external time source as follows:
- Open a command shell as administrator
- Enter:
w32tm /config /manualpeerlist:time.u.washington.edu /syncfromflags:manual /reliable:yes /update net stop w32time net start w32time
Microsoft article on time service configuration
Deprecated command: net time /setsntp:time.u.washington.edu
Chapter 4: Removing a domain controller
If you wish to remove a domain controller from an existing domain, follow these steps. NOTE: If you remove the last remaining domain controller for a domain, all Active Directory information from that domain will be permanently lost. In addition, removing the last domain controller from a domain requires Enterprise Administrator privileges.
- Make a copy of the netlogon.dns file from your domain controller’s <WINDIR>\SYSTEM32\CONFIG directory. <WINDIR> will usually be C:\WINDOWS. Do this first because it will be deleted by later steps.
- Click Start , click Run , type dcpromo , and then click OK .
- This starts the Active Directory Installation Wizard. Click Next .
- There is a check box in the Remove Active Directory screen. If this computer is the last domain controller in the domain, click to select the check box. Otherwise, click Next .
- In the next screen, set the password for the administrator account on the server after Active Directory is removed. Type the appropriate password in the Password and Confirm Password boxes, and then click Next .
- In the Summary screen, review and confirm the options you selected, and then click Next .
- The wizard begins the process of removing Active Directory from the server. After the process is finished, a message indicates that Active Directory was removed from the computer.
- Click Finish to quit the wizard.
- Restart the computer.
- Using the netlogon.dns file you made a copy of in step #1 as a point of reference:
- Use https://networks.uw.edu/ to remove all the SRV, CNAME, & A records for dcserver1.xyz.washington.edu (Use your own DC and domain here of course).
- Also remove the xyz.washington.edu A record pointing at the static IP for your domain controller.
DNS record caching may mean it takes some time for the old DNS information to no longer be present. During this time you may see some errors as clients and servers try to contact the demoted domain controller.
Chapter 5: Where to go from here
There is documentation available for Windows at the UW.
For help with a Windows domain that you administer or for general help with Windows at the UW, please send mail to help@uw.edu.
Please note that UW-IT can only provide support for the services that it offers and can only respond to specific questions.