- On This Page
- Network Connections You Have
- Locations where Do-It-Yourself Wireless is permitted
- Do-It-Yourself Wireless Responsibilities and Policies
- Configuring Your Wireless Router
NEW SERVICE ANNOUNCEMENT:
- McMahon Hall: Starting with the 2024/25 school year, UW-IT will be providing the campus standard Wi-Fi services to all rooms in McMahon Hall.
This is no longer considered a Do-It-Yourself Wireless site and residents should NOT provide their own wireless router.
Network Connections You Have
As a residence hall member, you currently have:
- Fast, reliable connectivity to the campus network and the Internet via data ports (100/1000 Mbit/s Ethernet) in your room
- UW wireless service in many common areas in UW residence halls
- Pervasive UW wireless service in most UW residence halls
Locations where Do-It-Yourself Wireless is permitted
The following locations do not have pervasive campus WiFi or only have coverage in common areas. Students are permitted to run their own wireless access points in their rooms, provided they adhere to the appropriate responsibilities and policies.
Do-It-Yourself Wireless Responsibilities and Policies
- In UW residence halls where wireless network service is provided by the UW
- Setting up personal wireless routers is prohibited in these buildings and your network outlet will be disabled if they are discovered. You should see a wireless network named “eduroam” or “University of Washington” available for your use. If you are unsure if service is available in your residence hall, check with your resident adviser.
- In other residence halls
- You have the option of installing your own wireless network and connecting it to the data port in your room.
Be aware of the following before you decide to install your own wireless access point (WAP):
- You must provide your own technical support for installation, configuration and ongoing maintenance of your equipment.
- You must comply with the network security policies of the University of Washington. (This means you are responsible for managing the security and activity of all computing devices on your wireless network.)
If you are willing to assume the above responsibilities for your own wireless network, please review the policies and specifically note that:
- Providing an open network connection that could be publicly accessed is prohibited.
- You must insure that your wireless network meets the security requirements outlined on the Web page above.
Configuring Your Wireless Router
The back of a typical wireless router is shown below:
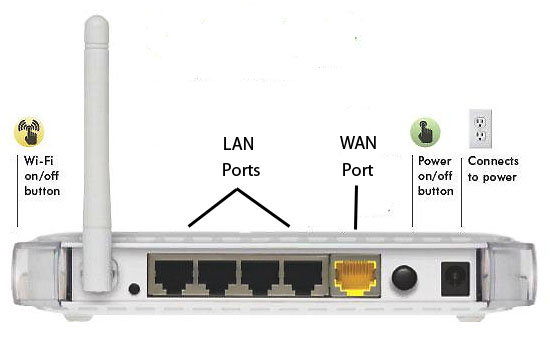
The WAN port (often colored yellow) is the one you should connect to the provided network outlet. If you connect the wall port to one of the other ports it may interfere with network use by others nearby and the wall port will be disabled.
The wireless router creates a local area network (LAN) and handles traffic going between the residence hall networks and the LAN.
- StepsActions
- Connect the cable from your computer to one of the LAN ports on the wireless router.
- Using the computer’s browser, go to the configuration menu for your router (see the router’s instructions).
- Use minimum power to reduce interference with other devices. In a residence hall, a wireless router that provides wider coverage may experience decreased performance due to interference with other wireless routers.
- Have a unique SSID. The name of your local network (the SSID) must be unique to avoid conflict and confusion with campus WiFi and other networks. In order to insure uniqueness between your network and other resident hall networks, consider using your name (or nickname) plus your room number.
- This step is very important for preventing conflict between your wireless router and others nearby!
- Use encryption that will require a password to connect. Use WPA2 or WPA.
- Use hardware (MAC) address registration. Rather than leave your wireless router open for anyone to access, explicitly allow your devices by entering their hardware addresses in the router’s access configuration. Hardware addresses are also called MAC (Media Access Control) addresses. Check your user manual for each device for how to find its MAC address.
- Using the hardware address method is important as it restricts use of your wireless router to specific computers you know about. Without such explicit protection, someone you do not know could access and use your wireless router. If their computer is infected and tries to send spam or malware through the connection, all use of your data port could be blocked.
- Turn on the router’s firewall, if one is available.
- Connect to the wall data port via the WAN or UPLINK port on your wireless router (normally the yellow port).
