- On This Page
- Two-factor authentication and Duo
- Expanding 2FA “on the web”
- Installing Duo
- Hardware tokens
- Using 2FA
- Troubles with 2FA
Questions not answered on this page? Try our main 2FA page or email help@uw.edu.
Two-factor authentication and Duo
What is two-factor authentication?
Two-factor, also called 2FA, adds a second layer of security when signing in. The UW uses Duo for 2FA. Normally, you verify your identity with a single factor, such as a password, which is something you know. Verifying your identity using a second factor, like a smartphone or hardware token, which is something you have, prevents others from signing in as you, even if they know your password.
Why do I need two-factor authentication?
Passwords can often be stolen, guessed or hacked, and you may not even realize your password has been compromised. With two-factor authentication protected services, a compromised password won’t mean a compromised account.
Why should I “opt in” early to 2FA?
You’re encouraged to utilize 2FA to “Lock down your login”. That way, you’re familiar with the process and ready for when the registration system, Canvas, MyUW and other systems require 2FA. Visit Opt in to use 2FA on the web.
Can I change my mind after I opt in?
No, once you opt in to 2FA, you cannot opt out, because a key security measure to safeguard data at the University is use of 2FA by students, faculty and staff.
Expanding 2FA “on the web”
What do you mean by 2FA “on the web”?
This refers to UW resources that rely on a web browser for handy “single sign-on” using your UW NetID and password.
When you use 2FA “on the web” at the UW, you will be protecting data in more systems. These include MyUW, Canvas, Panopto, UW Google, UW Exchange Online and many other web-based services that require UW NetID authentication. Some desktop and mobile apps, including Outlook, Zoom and Husky OnNet virtual private network (VPN), also rely on UW NetID sign-in via the web.
What is happening for students?
UW resources that rely on a web browser for single sign-on using UW NetID and password will start to require 2FA at a later date. After entering your UW NetID and password for a UW system or app that relies on a web browser for single sign-on, you will be prompted to verify your identity by using your 2FA/Duo device. Please always have your 2FA device (typically a smartphone) with you. Note: If you will be using a token instead of a phone or tablet and do not have the token available, you can get a temporary bypass code from the UW-IT Service Center; contact them at (206) 221-5000 or at help@uw.edu.
I would like to reduce the number of times I am prompted for 2FA. How can I do this?
- Easily reduce the number of times you are prompted to sign in with your 2FA device by clicking the “remember me” option on personal devices or on other non-shared computers that you regularly use and trust. “Remember me” tells your browser to remember that you have confirmed your identity using your 2FA device. If you select this option, you won’t have to use your 2FA device as often with that browser.
- Microsoft similarly offers “Stay signed in” for UW Entra ID; read more about this option to reduce 2FA/Duo prompts.
Installing Duo
How do I install Duo?
Instructions for installing Duo depend on what device you are going to use as your second factor:
- Smartphone or tablet: Smartphones and tablets are able to use the Duo Mobile app for authentication. Refer to Set up a smartphone or tablet.
- Mobile phone or landline: Phones can also be used via the “call me” authentication method. Refer to Set up a mobile phone or landline.
- Token: Hardware tokens are small security devices that support 2FA. Refer to Hardware tokens.
Is the Duo Mobile smartphone and tablet app free?
Yes.
What do I need to use Duo authentication?
To use Duo two-factor authentication, you will need either a smartphone or tablet that can run the Duo Mobile application, or a phone capable of receiving a voice call.
Signing into a web application protected by Duo requires a modern web browser with JavaScript enabled. Supported are Google Chrome, Mozilla Firefox, Safari, Edge, Opera or Internet Explorer (IE). For IE, version 8 or later is required.
To use the preferred Duo Push method of authentication, a smartphone or tablet with the Duo Mobile app installed is required. The most recent versions of operating systems are supported; for more information on older versions, see the Duo Mobile documentation. If you do not have a device capable of installing the Duo Mobile application, you can enroll a phone number that can receive a voice call to authenticate you.
If you are not able to use any phone-based authentication method, Duo also supports hardware tokens. Then, instead of relying on a phone, you can use the physical token that you would need to personally have in your possession. Learn more about hardware tokens.
If I get a new phone, what do I do?
If you get a new phone (or tablet) you will need to configure the Duo Mobile application on your new device, as it will not work automatically even if your old device had Duo installed.
- If you are keeping your same phone number, then you can use the “call me” method of authentication. Go to Identity Provider, 2FA tab, and add a new device via “Manage 2FA devices.” Once authenticated, you can select “Add a new device” or “Reactivate Duo Mobile.” Get details at Set up a smartphone or tablet.
- If you are not keeping your old phone number, you will either need to use your old phone for authentication or call the UW-IT Service Center at 206-221-5000, option 1, to get a temporary passcode. Once authenticated, you can enroll your device as above. Get details at Set up a smartphone or tablet.
Hardware tokens
Can I request a hardware token from UW-IT? Or register my own?
Yes. UW-IT will provide a hardware token if you need one. Or you can register your own, if it’s compatible. To learn more, refer to hardware tokens.
Do I need a device in order to request a token?
No. Request a token if you need one.
Using 2FA
How do I generate a passcode using the Duo Mobile application?
A passcode can be generated on the Duo Mobile application by tapping the bar containing ‘University of Washington’ inside the Duo Mobile application. You should then be shown a set of numbers which can be used to sign in at the Duo authentication prompt.
You also can generate a passcode with the Duo Mobile application even if your phone is not connected to the internet. Fortunately, generating a passcode with the app doesn’t use any data or minutes on your cell phone plan.
What if I have accessibility concerns with 2FA?
Duo has documented the steps they have taken for accessibility at https://duo.com/docs/accessibility.
The Duo prompt iframe has been designed by Duo to be more accessible including supporting most screen readers. A default authentication method can also be set to avoid having to select an authentication method.
For authentication methods the Duo Mobile application which can be used as a form of authentication is reported by Duo to work with smartphone accessibility technologies. The App can be used for “pushes” which is a prompt on the smartphone, or for generating a passcode.
Additionally with a phone based authentication method, the “call me” option can be easier to use, as this method requires answering a phone call.
Finally there do exist physical tokens that are not dependent on reading a passcode off of them. UW offers Hardware tokens, and supports personal hardware tokens that may be a better fit for accessibility like Yubikeys.
What can I do if I am offline or out of cellular service?
It’s important to understand and set up alternative methods of authentication that are available when you’re not connected:
- What if I have no service?:
- When you can, use the internet! Your Duo Mobile app can be used to approve authentications via the “Duo Push” method, even when you don’t have service. This is helpful when the building you are in blocks service or you are traveling but find wi-fi.
- What if I have no internet?
- Use passcodes on your Duo-enabled device! Your Duo Mobile app can be used to generate passcodes while not connected. Go to “Sign in with 2FA” near the bottom of the main 2FA page for more information. See the above question for more details
- Token:
- Hardware tokens are small security devices that support 2FA. They are another great resource when you are expecting to encounter trouble with other authentication methods. Refer to Hardware tokens.
- Security key:
- You can set up a security key (also known as Universal 2nd Factor, or U2F) device for Duo 2FA at UW. Refer to Set up a security key.
- Another phone:
- You can use a different phone as your alternative. Refer to Set up a mobile phone or landline.
Can I use Duo while outside of the United States?
While most devices and sign-in options may be used outside the United States, it is important to enroll the device(s) ahead of your travel time.
- If you’ll have reliable internet access on your device while abroad, Duo Mobile and its “Send Me a Push” option for signing in will work normally.
- If you won’t have internet access on your device, Duo Mobile can operate while offline using the “Enter a Passcode” options; follow the steps above to generate a passcode when you need to sign in. A hardware token will also work offline but, since it is a physical device, it is best to obtain the hard token before you begin travel. Refer to hardware tokens to learn more.
- Please note the “Call Me” option only works with phone numbers in the US (and parts of Canada). If you want to use this option, you must enroll in Duo using a US phone number and be able to receive calls to this number while abroad.
- Lastly, the following regions are affected by Duo OFAC restrictions and will block authentication attempts. If you are traveling to one of these regions, please contact UW-IT at help@uw.edu.
Impacted countries or regions:
- Cuba (CU)
- North Korea (KP)
- Iran (IR)
- Sudan (SD)
- Syria (SY)
- Crimea region (43)
- Donetsk region (14)
- Luhansk region (09)
- Sevastopol region (40)
Adding a device with an International Phone Number?
- The Duo 2FA system does not place calls to international phone numbers and only works with phone numbers in the US (and parts of Canada).
- You can successfully add an international phone number but the Call Me option will not be available to use.
- International compatible devices can still be added using the mobile phone option or the tablet option when using the DUO Mobile app.
- The DUO Push notification and the Passcode options are available if the device is configured as a mobile phone with an international number or as a tablet.
If your primary 2FA and back-up method(s) fail, contact the UW-IT Service Center for a bypass code. A support person will verify your identity and provide a bypass code that authorizes your UW NetID and password access. This bypass code will act as the critical second step for authentication.
Phone: (206) 221-5000 | Email: help@uw.edu
Visit the Lost or stolen 2FA device page on IT Connect for detailed information. Note that if you set up more than one 2FA device, you can use your available 2FA device to remove your lost or stolen device; go to the 2FA tab.
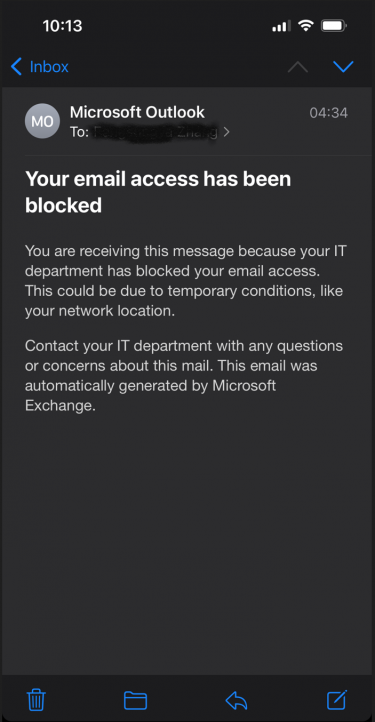
You may see an email in your UW inbox like this:
While the email message says it was sent by your IT department, it was not. This email message wasn’t actually sent–it only exists on your mobile device and was created to alert you to the fact that your client application can’t sign into your account. Your email access has not been blocked–it is only that this client application is broken. You can verify for yourself that your email access was not blocked by going to Outlook on the Web. And the reason the client application is broken is because it can only do legacy authentication OR it only has cached credentials which are based on legacy authentication.
One of three things likely happened to cause this error message:
- You are a student and have not opted into ‘UW Duo 2FA for the web’. As a result, you have been assigned a terms of use reminder screen. That screen is not compatible with legacy authentication and is invisible to you when you try to open your email client. You must accept it to continue, but you can’t see it. To resolve, you must either fix your email client or opt into 2FA. If you opt-in, the terms of use screen will no longer be present.
- You have opted into 2FA and are using an iPhone with 15.6 or better. In this scenario, Apple tries to automatically convert your cached legacy authentication credentials into cached modern authentication credentials silently. However, because 2FA is part of the experience, you must interact with something which is designed to be invisible to you. You may need to remove your UW account and re-add it in order to complete the process.
- You have waited beyond the deadline communicated to you and your use of legacy authentication has been blocked. To resolve, fix your email client.